Methods to Combat CLI Spoofing
CLI (Calling Line Identification) spoofing poses a serious challenge to the telecommunications industry, enabling fraudsters to manipulate caller IDs, eroding trust, and causing substantial financial and reputational harm for MNOs.
This article explores technical strategies to combat CLI spoofing, providing detailed methodologies, actionable insights, and best practices for effective implementation.
What are the methods to combat CLI Spoofing?
This non-exclusive list provides them from the simplest to the most advanced:
- Do Not Originate (DNO) Lists: These lists block calls from numbers that should never originate calls, like emergency lines or government numbers. By designating such numbers as „Do Not Originate,” telecom systems can immediately flag and block them as likely spoofed calls.
- Allow and Block Lists: These lists help categorize numbers into trusted (Allow List) and suspicious (Block List) groups. Trusted numbers bypass checks, while suspicious ones are blocked, enhancing fraud prevention dynamically.
- Location Check: Location Check verifies whether a caller’s network location corresponds to the expected activity. It uses location queries to detect mismatches, proactively identifying potential spoofing before calls connect.
- Roaming On-Call Check: This method verifies that subscribers genuinely make calls while roaming by analyzing signaling data. It ensures real-time validation using cached CAMEL network information to detect inconsistencies and prevent spoofing.
- Inter-Operator API: This approach enables real-time validation of caller identities by querying operators about the legitimacy of a caller ID. Responses from these queries classify calls as spoofed, legitimate, or requiring further scrutiny, enhancing cross-operator fraud detection.
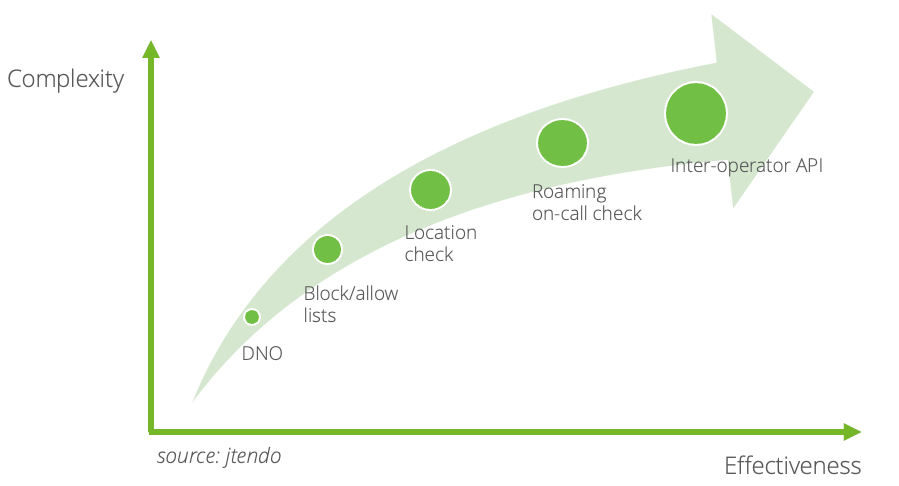
Let’s take a closer look at each of those methods.
Do Not Originate (DNO) Lists
Certain phone numbers (or ranges of numbers) should never originate calls – think government lines, financial services, or specific enterprise numbers. These numbers are marked as „Do Not Originate,” so if a call comes from one of these, it is flagged and blocked since it’s most likely spoofed.
There are two main approaches to setting up DNO:
- Centralized Register: In this model, a national or global database of DNO numbers is managed by a central authority. Telecom operators nationwide refer to this centralized list to block unauthorized calls in real-time.
- Guided Lists: NRA provides a framework and expects CSPs to compile their own DNO lists based on their recommendations. For example, FCC advises putting on the DNO list:
- Inbound Calls Only Numbers: Phone numbers assigned solely for receiving calls, not making them.
- Invalid Numbers: Numbers that fall outside the valid structure of the North American Numbering Plan (NANP).
- Unallocated Numbers: Valid NANP numbers that haven’t been allocated to any provider by the NANP Administrator. These numbers are in the system but not yet in use.
- Unused Numbers: Numbers that have been allocated but are confirmed as unused by the subscriber or the provider.
Several countries have already introduced DNO as part of their national efforts to reduce fraudulent calls:
- United States: The FCC introduced DNO lists as part of a broader anti-robocall campaign.
- United Kingdom: Ofcom implemented DNO rules to safeguard the integrity of emergency services and government numbers.
- Poland: DNO was the initial phase of the nationwide solution called Safe Harbor introduced by UKE, which jtendo helped to deliver.
Allow and Block Lists
Allow/Block Lists are configured within a system to detect and prevent fraud by filtering calls based on trusted or suspicious numbers. Calls from numbers on the Allow List are permitted without triggering fraud detection mechanisms, while numbers on the Block List are flagged or blocked due to suspicious activity.
Allow List
- The Allow List is for numbers that need to be explicitly trusted. Common examples include:
- Called numbers like MSRN (Mobile Station Roaming Number) for international calls or TSAN for home routing.
- Calling numbers that may involve legitimate spoofing – where a caller ID is intentionally altered for valid business reasons but with no fraudulent intent.
Block List
The Block List typically includes:
- DNO (Do Not Originate) numbers: These numbers should never originate calls, such as government or emergency lines.
- Unallocated national and international numbers: These numbers are either not assigned or don’t conform to the national numbering plan, making them prime candidates for fraud.
- AI/ML-detected fraud patterns: Numbers that are identified by AI as being linked to fraud schemes like IRSF, Wangiri, or PBX hacking are automatically flagged and added to the Block List.
- Robocalls/flash call patterns: Numbers associated with spammy, automated call behaviors (like robocalls) are identified and blocked based on repetitive patterns.
What is essential for Allow and Block Lists?
- Real-time efficiency: Block Lists need to operate instantly, even when managing millions of entries.
- Pattern flexibility: Instead of listing specific numbers, the system should use prefixes or regular expressions to detect patterns, making fraud detection more versatile.
- Automated updates: Dynamic management via AI-powered feedback loops ensures that lists remain current and effective as fraud patterns evolve.
- Flexible responses: Blocking isn’t always the only action – calls can be flagged or caller ID restrictions (CLIR) applied based on list matches.
Location Check
Location Check is a feature that allows telecom operators to determine if a given number is registered in the visited network (roaming) or home network. This process involves sending a location query (e.g., MAP SRI_For_LCS) to the Home Location Register (HLR) to obtain location data, specifically the network node number corresponding to the Visitor Location Register (VLR) number. The fundamental premise is that if a calling party is recognized as an own mobile number and its location doesn’t indicate roaming, such a call should never appear on interconnect links. If it does, it’s likely a spoofed call.
Specific Call Scenarios
While the basic principle is straightforward, several specific scenarios need to be considered:
- Roaming: When a subscriber is registered in a foreign network, the call is allowed as the location indicates roaming. Even if those two locations differ.
- Call Forwarding: Calls that are forwarded, either domestically or internationally, are recognized and allowed if they originate from a home network. The system must accurately identify these scenarios to prevent false positives.
- Freephone/Infoline Services: Calls involving service numbers that translate into target numbers within the same network require specific handling.
- Call Transfers and Completion: Like forwarding scenarios, these require careful configuration to ensure legitimate calls are not blocked while preventing spoofed ones.
Benefits of Location Check
- Proactive Detection: Unlike CDR-based methods, Location Check can detect potential spoofing attempts before connecting the call.
- High Accuracy: This method provides a strong indicator of call legitimacy by verifying the subscriber’s actual location.
- Reduced False Positives: When properly implemented, Location Check can significantly reduce false positives compared to other methods.
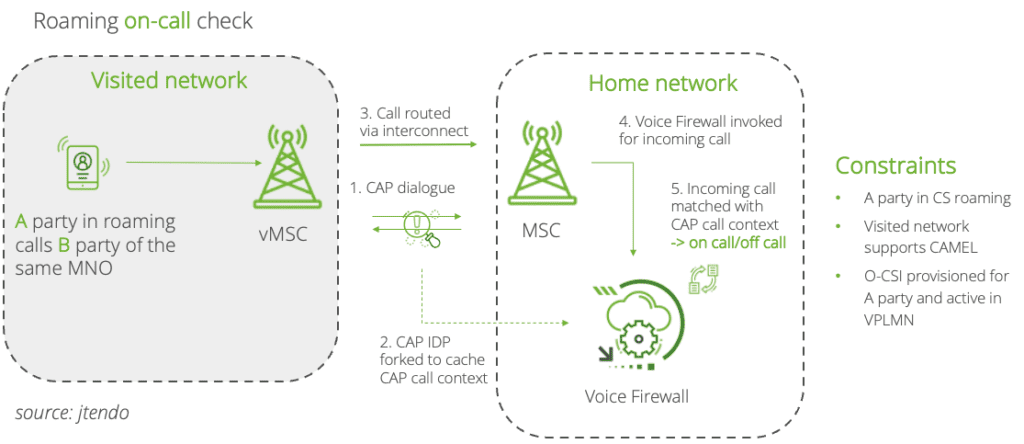
Roaming On-Call Check
1️. Network-Specific Application: CAP call context is applicable exclusively to CAMEL networks, where it can be used to verify the origin of calls by analyzing signaling data for inconsistencies that may indicate spoofing.
2️. Traffic Gathering Methods: Multiple methods are available to gather CAP traffic from the network, including probes and monitoring tools that capture signaling messages.
3️. Real-Time Challenges: Implementing CAP call context analysis in real-time poses significant challenges. The Initial Detection Point (IDP) must be cached instantaneously to avoid introducing delays in the call setup process.
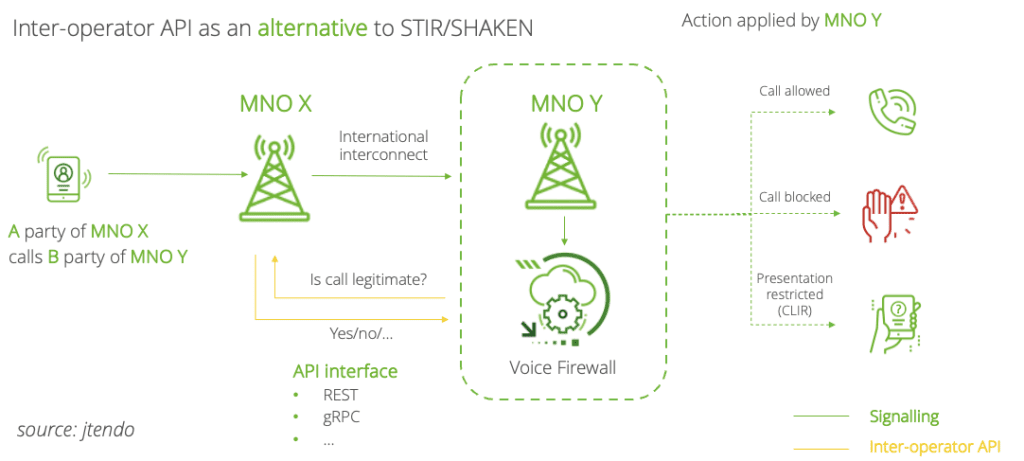
Inter-operator API
The main objective of Inter-operator API is to validate a calling party number from a call coming from an untrusted source (trunk). Suppose an MNO receives a call via international links with a calling party number belonging to another operator from the same country. In that case, he may use API to query this operator for information on whether this subscriber is really roaming.
Things to consider
- Flexible Implementation: Verification is dependent on each operator’s infrastructure and protocols. Different methods described in previous posts can be used.
- Protocols: The API can utilize different protocols like REST or gRPC, providing flexibility in communication. Each operator exposes standardized API functionality, facilitating seamless integration and cooperation.
Response Variability
- Definitive Responses: The API may return a response indicating that a call is definitively spoofed, allowing for immediate blocking or alerting actions.
- Uncertain Responses: In cases where the operator is uncertain, the API might return a less definitive response, prompting further investigation or monitoring.
Summary
Combatting CLI spoofing requires a combination of robust strategies, including DNO lists, dynamic Allow/Block Lists, Location Checks, Roaming On-Call Checks, and Inter-Operator APIs. Each method brings unique strengths, offering proactive detection, real-time validation, and collaboration across networks to reduce fraudulent calls effectively. By implementing these measures, telecom operators can safeguard their networks, protect their customers, and restore trust in communication systems. A multi-layered defense approach is essential to address the ever-evolving threats of CLI spoofing.





